There’s a useful tool called bettercap that claims to be the “Swiss Army knife for WiFi, Bluetooth Low Energy, wireless HID hijacking and Ethernet networks reconnaissance and MITM attacks”.
While you might want to use it to test Bluetooth LE security, a more interesting use is for debugging Bluetooth LE. If you are scanning for advertising or creating or using GATT, for example with a beacon, it’s sometimes useful to have a separate way of exercising Bluetooth LE.
Bettercap is written in Go and runs on GNU/Linux, BSD, Android, Apple macOS and the Microsoft Windows. However, a bug in Windows and macOS prevents the Bluetooth commands from working. Hence, it’s for Linux or Android only.
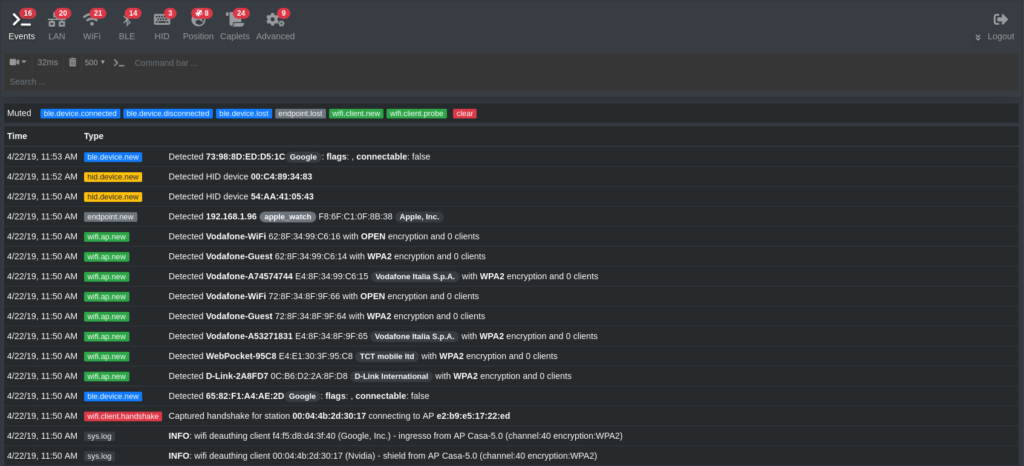
Better caps runs in the browser and you can create scripts.
UPDATE: There’s a tutorial on Medium.