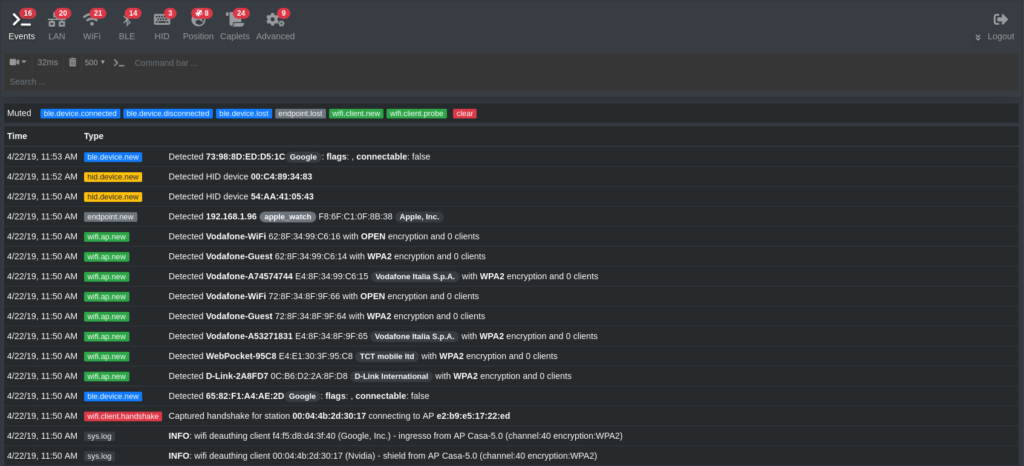
Renaud Lifchitz, a security consultant, has some great new slides on Security review of proximity technologies: beacons and physical web.
He mainly concludes that:
- Beacons can easily be spoofed
- Beacon passwords are often sent in plain text
- Web Bluetooth might be used with XSS to allow hacked sites to access local devices via GATT
The spoofing issue is well known and is a necessary consequence of a broadcast, non-connectable, type mechanism. Fortunately, people mainly only use these things for nefarious purposes when there’s a profit motive. Spoofing beacons rarely benefits anyone.
The beacon passwords thing sometimes happens when beacons are set up using the manufacturer app. This is usually a one-off event, when the beacon is first set up, when the user is usually control who in their surroundings. Hence, it’s very unlikely other people will ‘sniff’ the beacon password.
For Web Bluetooth, GATT communications without a known password is benign. You can’t do much by just connecting to a beacon or Bluetooth device. You usually need a password to change or view security sensitive data.
While it’s good to know these things, it’s very unlikely any of these security observations will ever be a problem. Beacons don’t tend to be used in critical or valuable scenarios so the risk of things being subverted is low. There are much easier, more valuable and higher profile targets for hackers in the shape of servers, desktops, laptops and apps. Even if one of the mechanisms mentioned in the slides were used one day, the consequences, for most scenarios, would be minimal.