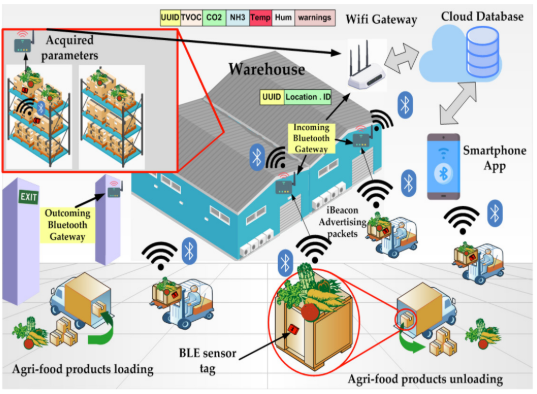
Nordic Semiconductor has a recent article by Petter Myhre Jun on Wireless Solutions Take Sports Tracking to New Level.

Petter talks about how location and movement sensors can be used to take athletic measurements for monitoring, analysis and performance improvement. He describes the SpoSeNs 2.0 Professional Wearable built round Nordic Semiconductor’s nRF52840 SoC.
However, many types of sports measurement can be implemented using off the shelf sensors. Standard beacons can be used for locating and Bluetooth sensors with accelerometers used for finer measurement of movement.





It’s also possible to measure heart rate that can lead into health related applications. We previously worked on Ultimate Sport Service’s heart rate tracking project. Ultimate Sport provide running race timing solutions. The heart rate tracking project allows Ultimate Sport to collect and display the real-time heart rates of a group of runners.
BeaconZone was a key part in succeeding with our custom heart rate tracking project. From assessing potential challenges in the Bluetooth framework on iOS and Android to evaluating hardware possibilities, we got valuable and accurate advice. The project was delivered on time and we are confident we will be working together again in the future.
Ultimate Sport Service Aps, Denmark