Researchers from TU Darmstadt, Germany have a new paper Toxic Friends in Your Network: Breaking the Bluetooth Mesh Friendship Concept that looks into weaknesses in the security model underlying the Bluetooth mesh friendship mechanism.
Friendship allows a low-power IoT device to go to sleep with a separate higher-power node caching packets until the lower power device wakes up. The paper provides an overview of friendship and the Friendship Security Material(FSM) unique to this type of communication.
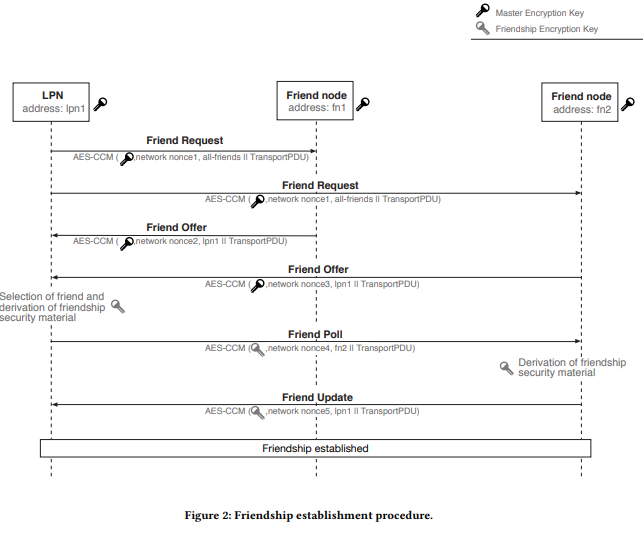
The researchers found three flaws in the Bluetooth friendship mechanism related to:
- The possibility of eavesdropping on communication and selectively jamming based on size of the control messages.
- The lack of protection of the friend security keys against an insider attack.
- The possibility of misuse of Friend Clear messages to cause a form of denial of service attack through flattening the battery.
The paper includes a reference to tools that demonstrate these problems and discusses possible mitigations.
The Bluetooth SIG responded:
Compromise of the friendship relationship results only in a compromise of the availability of the low power node to the other nodes in the subnet.
It is the conclusion of the working group that the friendship relationship between an LPN and its friend within a mesh subnet is not intended to be secured against attack by a party already in possession of the network key.
It is the position of the Mesh Working Group and the Bluetooth SIG that neither scenario provides additional security risk for a user of the Mesh profile
In other words, the risks are appropriate to the level to which the mesh is expected to be used or attacked.
We have yet to come across any devices using friendship. Friendship is an edge case that isn’t required in most instances. Also, most existing low power devices can’t be upgraded to use mesh due to the higher memory requirement of Bluetooth Mesh.
Read about Beacons and the Bluetooth Mesh