New vulnerabilities, called SweynTooth, have recently been found in Bluetooth LE. The problems aren’t in Bluetooth itself but in software development kits (SDKs) provided by some System on a Chip (SoC) manufacturers.
There are three types of problem that can be triggered by sending particular data to Bluetooth devices: crash, deadlock and security bypass. Only some manufacturer’s SDKs are affected and only some of their SoCs models.
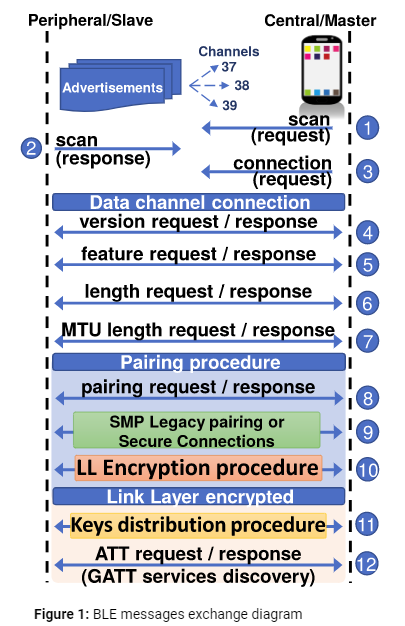
Texas Instruments, NXP, Cypress, Dialog Semiconductors, Microchip, STMicroelectronics and Telink Semiconductor SDKs are affected. The main manufacturer used in beacons in beacons and gateways is Nordic so the majority of beacons are not affected. Nevertheless, there are a few beacon models that use Texas Instruments and Dialog Semiconductors SoCs. Of these, very few use the specific affected SoC models.
The only affected devices we stock are the ABKey01, TON9128, TON9118, TON9108 that use the Dialog DA14580 SoC. You should avoid using these in critical scenarios because they can be caused to crash or deadlock. No beacons are vulnerable to the security bypass vulnerability.
As with all security issues, you have to put the possible attacks into perspective. The vulnerabilities are difficult to exploit in practice and it’s usually much easier to steal a beacon or remove its battery to make it inoperable.
The vulnerabilities are of more concern for critical medical devices such as pacemakers and blood glucose monitors.